Phishing Hacker Technique, Vectors
By A Mystery Man Writer
Last updated 12 Jun 2024

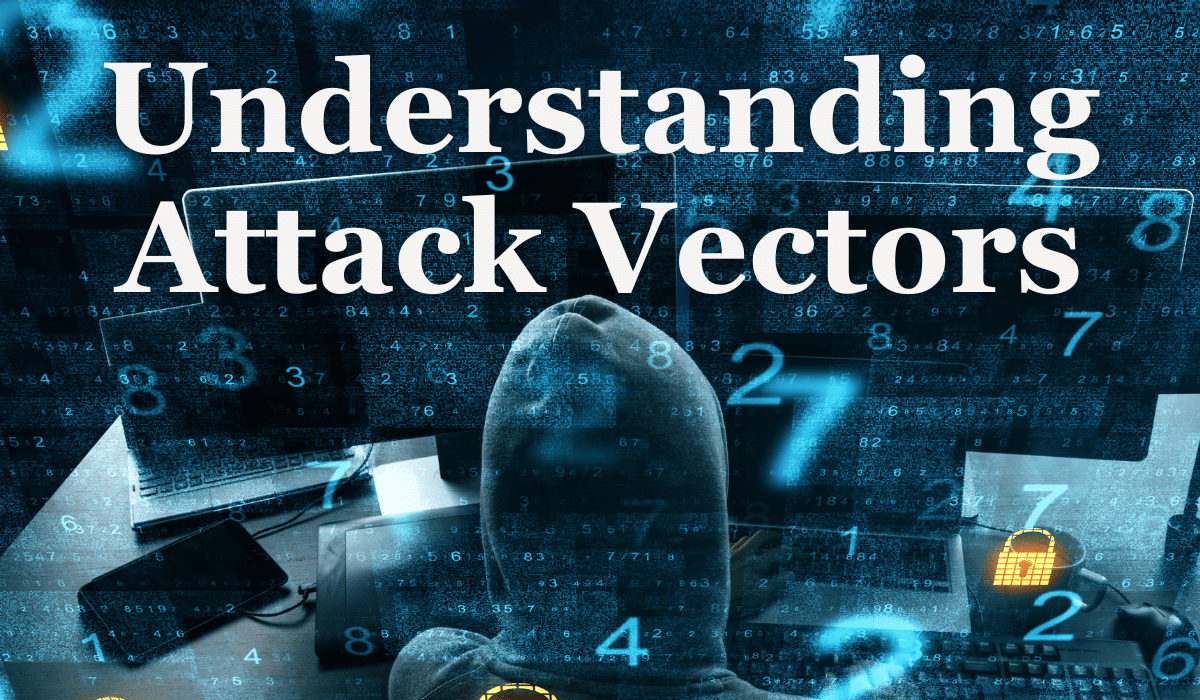
Understanding Active and Passive Attack Vectors - Breach Secure Now!

How Hackers Phish for Your Users' Credentials and Sell Them

Prevent email phishing attacks this summer with 3 defensive measures

Phishing technique used to steal digital data Vector Image
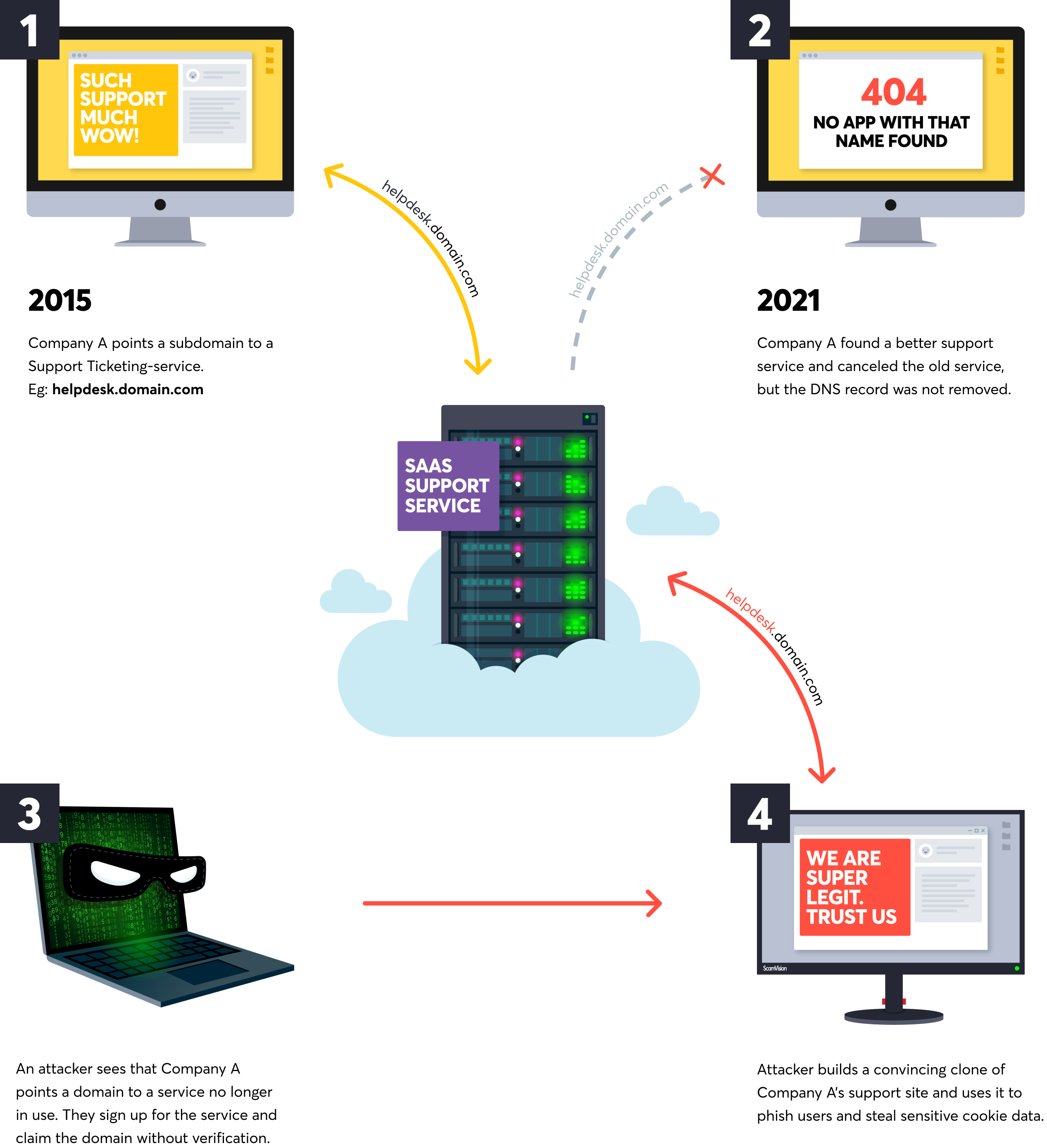
Attack Vector - Ultimate Guide

5 Phishing Techniques Organizations in the MENA Region Should Be Aware of - Kratikal Blogs
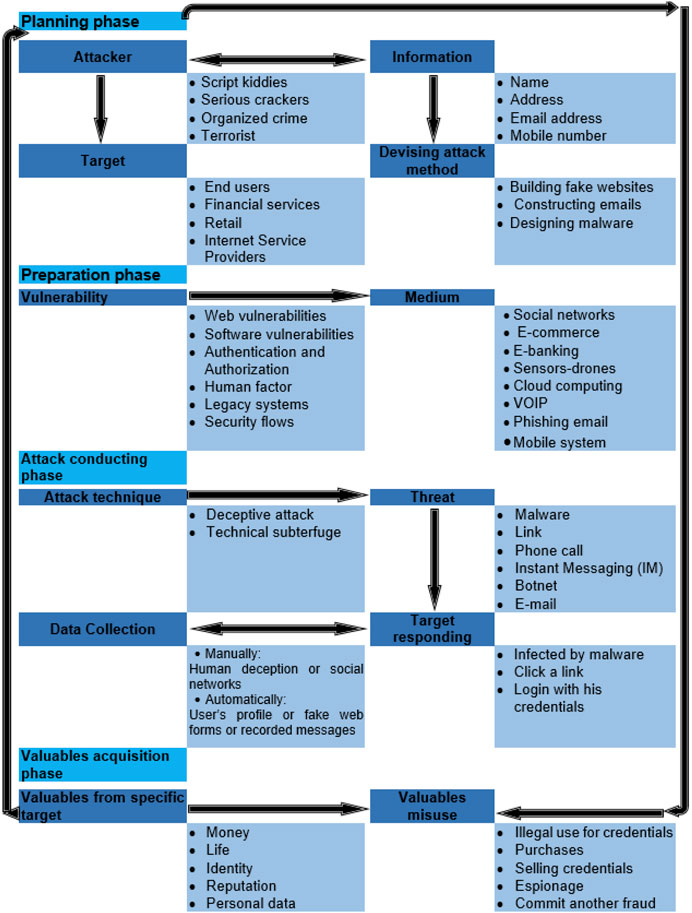
Frontiers Phishing Attacks: A Recent Comprehensive Study and a New Anatomy

Phishing Techniques and Preventative Measures
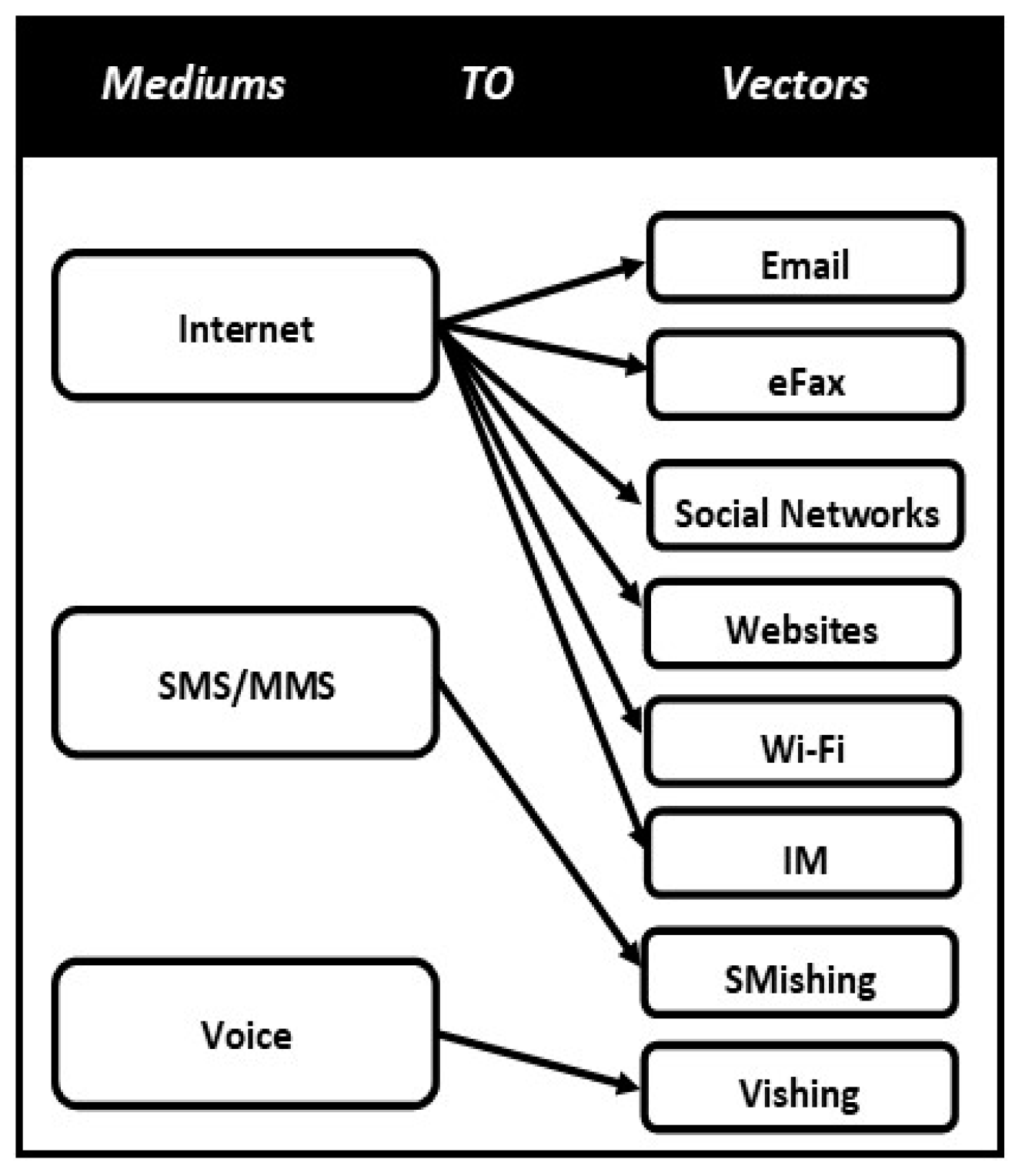
Future Internet, Free Full-Text

The Rising Threat of Credential Phishing: 10 Basic Ways to Safeguard Your Business - Bolster AI

Types Of Cyber Attacks Cyber Security Attack Vectors
Recommended for you
 Instagram Hacker Targets Fisherman14 Jul 2023
Instagram Hacker Targets Fisherman14 Jul 2023 Everyone has 'good time' at Camp L.E.A.P., Community14 Jul 2023
Everyone has 'good time' at Camp L.E.A.P., Community14 Jul 2023 Fishing for hackers: Analysis of Linux Server Attack14 Jul 2023
Fishing for hackers: Analysis of Linux Server Attack14 Jul 2023 A cyber thief is stealing money with fishing rod from the laptop. Online fraud concept. Phishing attack, fishing, hacker, web security, cyber thief Stock Vector Image & Art - Alamy14 Jul 2023
A cyber thief is stealing money with fishing rod from the laptop. Online fraud concept. Phishing attack, fishing, hacker, web security, cyber thief Stock Vector Image & Art - Alamy14 Jul 2023 Sports Fishing for Kingfish off Cronulla is FUN !!!14 Jul 2023
Sports Fishing for Kingfish off Cronulla is FUN !!!14 Jul 2023 DUO Hacker Slaver VIB 55 Mat Tiger NEW Fishing Lure #ED1814 Jul 2023
DUO Hacker Slaver VIB 55 Mat Tiger NEW Fishing Lure #ED1814 Jul 2023- Ever since I discovered this one fishing hack, my entire world of fishing changed. Fishing braid is great. It's super sensitive, no str14 Jul 2023
 Brandon Hacker's Chinook and Matt Mantia's brown trout share Fish14 Jul 2023
Brandon Hacker's Chinook and Matt Mantia's brown trout share Fish14 Jul 2023 Stern of the fishing boat Esther Louis, Morro Bay14 Jul 2023
Stern of the fishing boat Esther Louis, Morro Bay14 Jul 2023 Premium Vector Data phishing hacking online. scam envelope14 Jul 2023
Premium Vector Data phishing hacking online. scam envelope14 Jul 2023
You may also like
 PE Rope Golden for Middle East 3 Strand Twine Builder Line Polyethylene String Mason - China PE Rope and PE Twine price14 Jul 2023
PE Rope Golden for Middle East 3 Strand Twine Builder Line Polyethylene String Mason - China PE Rope and PE Twine price14 Jul 2023 Time Forest Curtain Rod Wall Bracket Hooks, Set of 2 (Silver)14 Jul 2023
Time Forest Curtain Rod Wall Bracket Hooks, Set of 2 (Silver)14 Jul 2023 New Fashion Female Spring Beanies Skuliies Autumn Warm Scarf Two14 Jul 2023
New Fashion Female Spring Beanies Skuliies Autumn Warm Scarf Two14 Jul 2023 VMC® Teams Up with Ice Fishing Guru Tony Roach on New Rattling Roach Spoon14 Jul 2023
VMC® Teams Up with Ice Fishing Guru Tony Roach on New Rattling Roach Spoon14 Jul 2023 HTF-Disney Store Mickey Mouse Magnetic Fishing Play Set Toy Rod14 Jul 2023
HTF-Disney Store Mickey Mouse Magnetic Fishing Play Set Toy Rod14 Jul 2023 Rapala Ott's Garage Slim Series Crankbait - FishUSA14 Jul 2023
Rapala Ott's Garage Slim Series Crankbait - FishUSA14 Jul 2023 Antique Fishing Nets & Floats for sale14 Jul 2023
Antique Fishing Nets & Floats for sale14 Jul 2023 Raguel cold weather fishing gloves14 Jul 2023
Raguel cold weather fishing gloves14 Jul 2023 My Fair Lady: 4 Track 7 1/2 IPS Reel to Reel: (1963) - Music14 Jul 2023
My Fair Lady: 4 Track 7 1/2 IPS Reel to Reel: (1963) - Music14 Jul 2023 How to Catch Kokanee14 Jul 2023
How to Catch Kokanee14 Jul 2023
